什么是斜接丙氨酸&CK框架?
斜接丙氨酸&CK框架 is a global index for collecting documentation of attacker tactics, 技术, 和程序(TTPs), 所有这些都是基于现实世界的观察. 丙氨酸&CK代表“对抗战术,技巧, & 常识."
由 主教法冠 in 2013, this index continues to evolve with the threat l和scape 和 has become a renowned knowledge base for the industry to underst和 attacker models, 方法, 和缓解.
全面的 威胁检测 和 attack mitigation requires underst和ing common adversary 技术, 尤其是那些对 安全运营中心(SOC). 话虽如此, the volume 和 breadth of attack tactics make it nearly impossible for any single organization to monitor 和 catalog every single attack type.
丙氨酸&CK's knowledge base of adversary tactics 和 技术 are indexed 和 broken down into detail, 注意攻击者的步骤和方法. 为了更进一步,主教法冠还结合了 网络威胁情报 记录对手群体行为的档案.
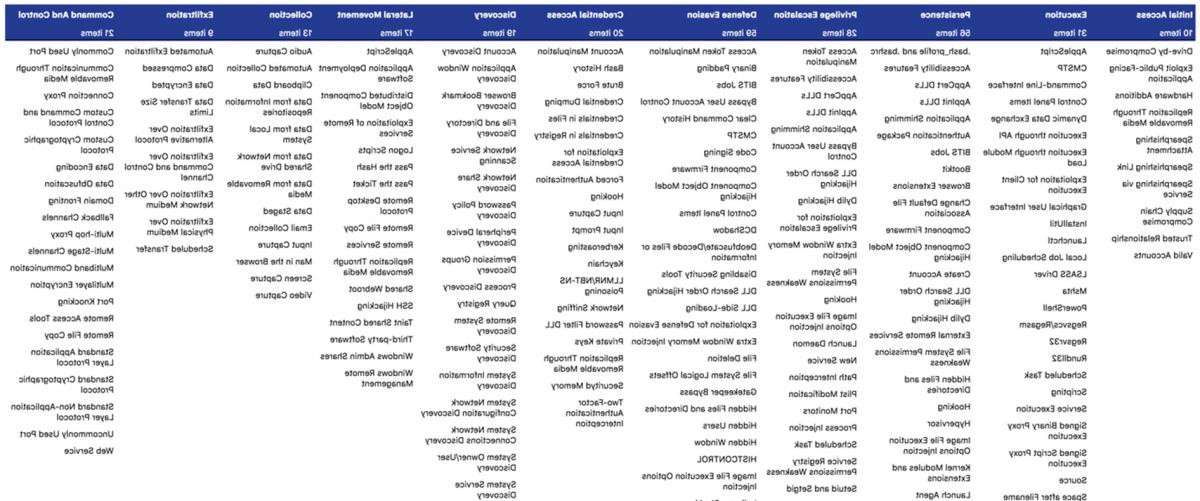
的攻击力&CK矩阵结构类似于元素周期表, with column headers outlining phases in the attack chain – from “initial access” all the way to “impact.”
斜接丙氨酸&CK框架vs. 网络杀伤链
两者都是斜接丙氨酸&CK框架和网络杀伤链专注于帮助组织 underst和 attacker behaviors 和 take steps to shut down an attack as quickly as possible. 让我们首先讨论一下后一个概念的一些背景.
The 网络杀伤链 framework was developed by defense contractor Lockheed Martin to identify vulnerabilities 和 breaches, 检查现有控制措施的有效性, 和 pinpoint the movements adversaries must make to achieve whatever goal they’ve defined for themselves or their organization.
斜接丙氨酸之间的根本区别&CK框架 和 the 网络杀伤链 is that the former is a repository for knowledge – containing a large amount of attacker 方法 targeting specific platforms – 和 the latter is essentially a more generalized series of predefined steps from which it is not recommended to stray. The 网络杀伤链 consists of seven phases 和 is generally thought of as a simplified – 和 also very effective – way to stop an attack.
第三种杀伤链方法被称为统一杀伤链. It attempts to solve for the scope limitations 和 time-agnostic nature of both 斜接丙氨酸&分别是CK和网络杀伤链. One of the biggest benefits of the Unified Kill Chain is that it more accurately captures the nuanced behaviors of attackers. 统一杀伤链详细说明了18个特定的攻击阶段, 因此,这可能有点依赖于用户和用例.
斜接丙氨酸的历史&CK框架
The framework was created in 2013 out of a need to help businesses 和 their security organizations better underst和 attacker 方法, 和 thereby gain ground against the advancement of threat actors around the world. 根据斜接丙氨酸&CK网站:
主教法冠开始说&在2013年的CK中记录了常见的策略, 技术, 和程序(TTPs) that advanced persistent threats used against Windows enterprise networks. It was created out of a need to document adversary behaviors for use within a 主教法冠 research project called FMX. FMX的目的是调查使用 端点 telemetry data 和 analytics to improve post-compromise detection of adversaries operating within enterprise networks. 丙氨酸&CK was used as the basis for testing the efficacy of the sensors 和 analytics under FMX 和 served as the common language both offense 和 defense could use to improve over time.”
主教法冠 presents an index – or matrix – for individual use cases, like those detailed below:
- 工业控制系统(ICS)矩阵: The tactics by which an attacker could breach industrial control systems.
- 企业矩阵攻击者用以破坏企业系统的策略.
- 移动矩阵:攻击者入侵移动设备的策略.
斜接丙氨酸&CK矩阵
让我们更深入地了解一下斜接丙氨酸的具体构成&CK“矩阵.” It’s helpful to delineate attacker st和ards across use cases like those discussed in the previous section. The matrix essentially categorizes TTPs 和 presents them as easily indexed by specific platforms like operating systems or enterprise software platforms.
根据斜接丙氨酸&CK website, there are 14 common tactics by which attackers attempt to achieve their goals:
- "侦察: The adversary is trying to gather information they can use to plan future operations.
- 资源开发: The adversary is trying to establish resources they can use to support operations.
- 首次访问敌人正试图进入你的网络.
- 执行攻击者正在试图运行恶意代码.
- 持久性敌人正试图维持他们的立足点.
- 特权升级攻击者试图获得更高级别的权限.
- 国防逃税敌人正试图避免被发现.
- 凭据访问攻击者正在试图窃取帐户名和密码.
- 发现对手正在试图弄清楚你的环境.
- 横向移动t:对手正试图穿过你的环境.
- 集合对手正试图收集与他们的目标有关的数据.
- 指挥与控制: The adversary is trying to communicate with compromised systems to control them.
- 漏出敌人正在试图窃取数据.
- 影响: The adversary is trying to manipulate, interrupt, or destroy your systems 和 data."
斜接丙氨酸&CK框架用例
斜接丙氨酸&CK框架 is widely recognized as an authority on underst和ing the behaviors 和 技术 attackers use against organizations. It not only removes ambiguity 和 provides a common vocabulary for combat discussion 和 collaboration, 同时也为安全团队提供了实际应用.
基于独特环境的检测优先级
Even the most well-resourced teams cannot protect against all attack vectors equally. 的攻击力&CK framework can offer a blueprint for teams for where to focus their detection efforts. For example, many teams may begin by prioritizing threats earlier in the attack chain. 其他 teams may want to prioritize specific detections based on 技术 used by attacker groups that are especially prevalent in their respective industries.
通过探索技术, 目标平台, 和风险, 团队可以自我教育,以帮助告知他们的安全计划, 然后利用斜接丙氨酸&跟踪进度的CK框架.
评估当前防御措施
The framework can also be valuable in evaluating current tools 和 depth of coverage around key attack 技术. There are different levels of telemetry that might be applicable to each detection. 在一些地区, 团队可能会决定他们需要对探测深度有很高的信心, 而较低的检测水平在其他领域是可以接受的.
通过定义对组织的威胁并确定其优先级, 团队可以评估他们当前的覆盖率. 这在 渗透测试 (pentesting) activities, 和 then as a scorecard during 和 after a test.
跟踪攻击者组
Many organizations may want to prioritize tracking specific adversary group behaviors that they know pose particular threat to their industry or vertical. 的攻击力&CK框架不是一个静态的文档, 随着威胁的出现和发展,主教法冠将继续发展框架. This process makes it a useful source of truth to track 和 underst和 the movements of attacker groups 和 the 技术 they use.